EU Cyber Resilience Act
Article 14 Reporting Obligations of Manufacturers
Complete workflow of all actors involved in the reporting process and the steps they must take
💡 Key Points
- Application date: Article 14 applies from 11 September 2026 (before full CRA compliance)
- Products in scope: Applies to any products placed on market when vulnerabilities/incidents occur
- Where to report: All notifications go through ENISA's Single Reporting Platform (SRP)
Reporting Process Overview
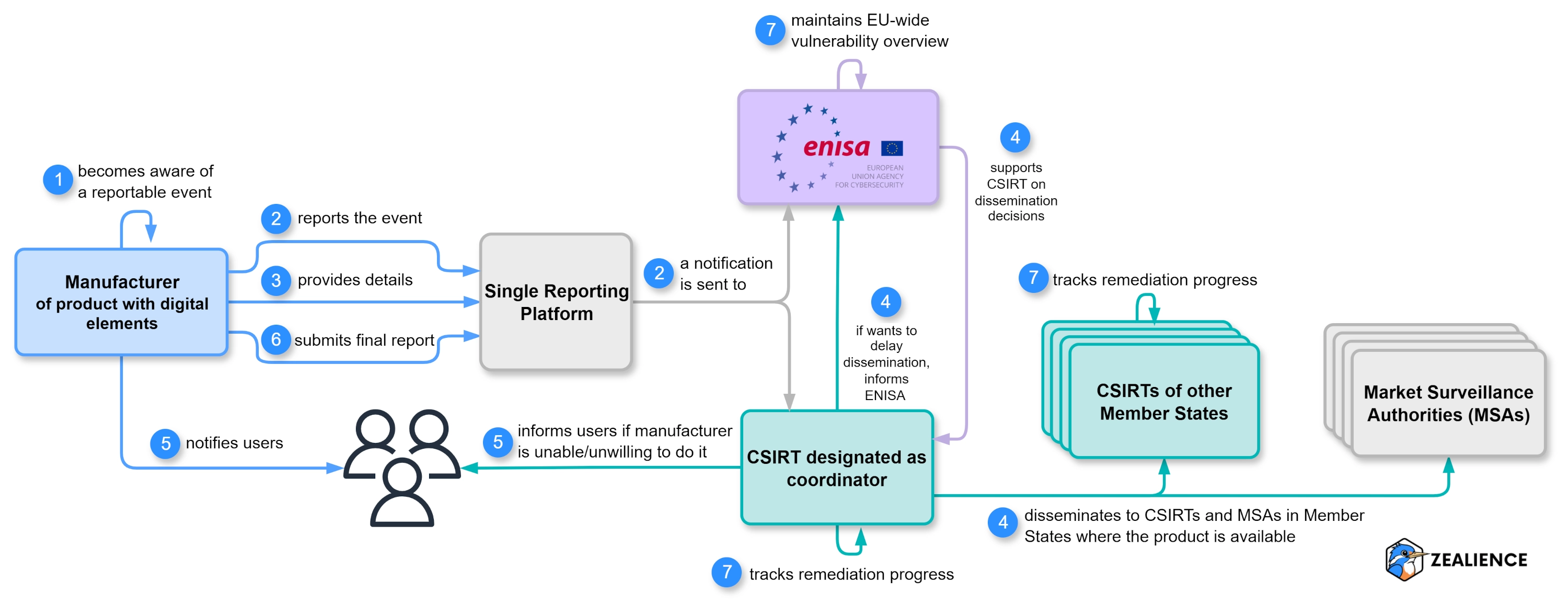
1 Discovery of a Security Event to be Reported
⚠️ Manufacturer Becomes Aware of Either:
- Actively exploited vulnerability: Exploitation of a vulnerability in a product on the market, resulting in its users being impacted
- Severe incident having an impact on the security of the product: Attack on the manufacturer's systems that has the potential to create downstream cybersecurity risks
2 Submission of an Early Warning Notification
⏱️
Timeline: Within 24 hours of becoming aware
Manufacturer must submit an "early warning notification" without undue delay
🏭 Manufacturer
Submits notification via Single Reporting Platform (SRP):
- Must contain the Member States where product has been made available
- Is sent to the CSIRT designated as coordinator
🛡️ CSIRT Designated as Coordinator
This CSIRT is determined differently for manufacturers:
- EU manufacturers: Main establishment location
- Non-EU manufacturers: Authorized rep./importer/distributor/users location
🌍 ENISA
Operates the SRP and serves as a strategic coordination hub
- Receives notification at the same time as CSIRT
- Has EU-wide visibility into security events reported
3 Detailed Notification
⏱️
Timeline: Within 72 hours of becoming aware
This notification is not needed if the relevant information was already provided in early warning
📋 Manufacturer Provides Further Details About the Security Event
For vulnerabilities:
- Product information
- Nature of exploit & vulnerability
- Corrective/mitigating measures taken
- Measures users can take
- Level of information sensitivity
For incidents:
- General info regarding the nature of incident
- Initial assessment of the incident
- Corrective/mitigating measures taken
- Measures users can take
- Level of information sensitivity
4 CSIRT Notification Processing & Dissemination
ℹ️
This step may occur before Step 3
Depending on the information already provided as part of the early warning notification, the CSIRT may start dissemination earlier
⚡ CSIRT Disseminates
Without delay, disseminates to:
- CSIRTs in Member States where the product is available
- National market surveillance authorities
Exceptional delays allowed:
- Manufacturer marked the notification to be kept confidential for some time
- CSIRT must inform ENISA of delay + justification
5 User Notification (Parallel Obligation)
👥 Manufacturer Informs Users
Must inform:
- Impacted users (always)
- All users (where appropriate)
Must include:
- Vulnerability/incident details
- Risk mitigation measures
- Corrective measures users can deploy
⚠️ If Manufacturer Fails
CSIRTs may step in and provide information directly to users if:
- Manufacturer doesn't inform users timely
- CSIRT considers it proportionate
- CSIRT deems it necessary to prevent/mitigate impact
6 Final Report
⏱️
Timeline Varies by Event Type
Vulnerabilities: Within 14 days after corrective/mitigating measure available
Incidents: Within 1 month after incident notification (stage 3)
This report is not needed if the relevant information was already provided earlier
Incidents: Within 1 month after incident notification (stage 3)
This report is not needed if the relevant information was already provided earlier
📄 Manufacturer Submits Final Report
For vulnerabilities:
- Description (severity & impact)
- Malicious actor information (if available)
- Security update/corrective measure details
For incidents:
- Detailed description (severity & impact)
- Threat type or root cause
- Applied and ongoing mitigation measures
📑 CSIRT May Request Updates
- Can request intermediate reports on status updates
- Monitors ongoing situation
- Ensures comprehensive documentation
7 Ongoing Monitoring & Coordination
🔍 CSIRTs Network
- Share information across EU Member States
- Coordinate responses to cross-border threats
- Support market surveillance authorities
- Track remediation progress
🎯 ENISA Analytics
- Aggregates vulnerability data EU-wide
- Identifies trends and patterns
- Supports NIS2 implementation
- Informs cybersecurity policy